DoT has asked users to beware of new types of scams. The telecom regulator has also prohibited people from downloading photos, videos, etc. from instant messaging apps like WhatsApp, Telegram.
Hackers these days send dangerous malware to users’ phones through photos and videos, which steals their bank account details. The Department of Telecommunications has also suggested some measures to avoid such scams.
New Dangerous Scam
Smartphones have become a necessity these days. Users use their phones not only for calling, but also to access UPI transactions, banks, etc.
In such a situation, if you get access to the phone in the hands of someone, then your bank account can be breached. Scammers are always trying to scam people by adopting new ways. This type of scam is called Steganography.
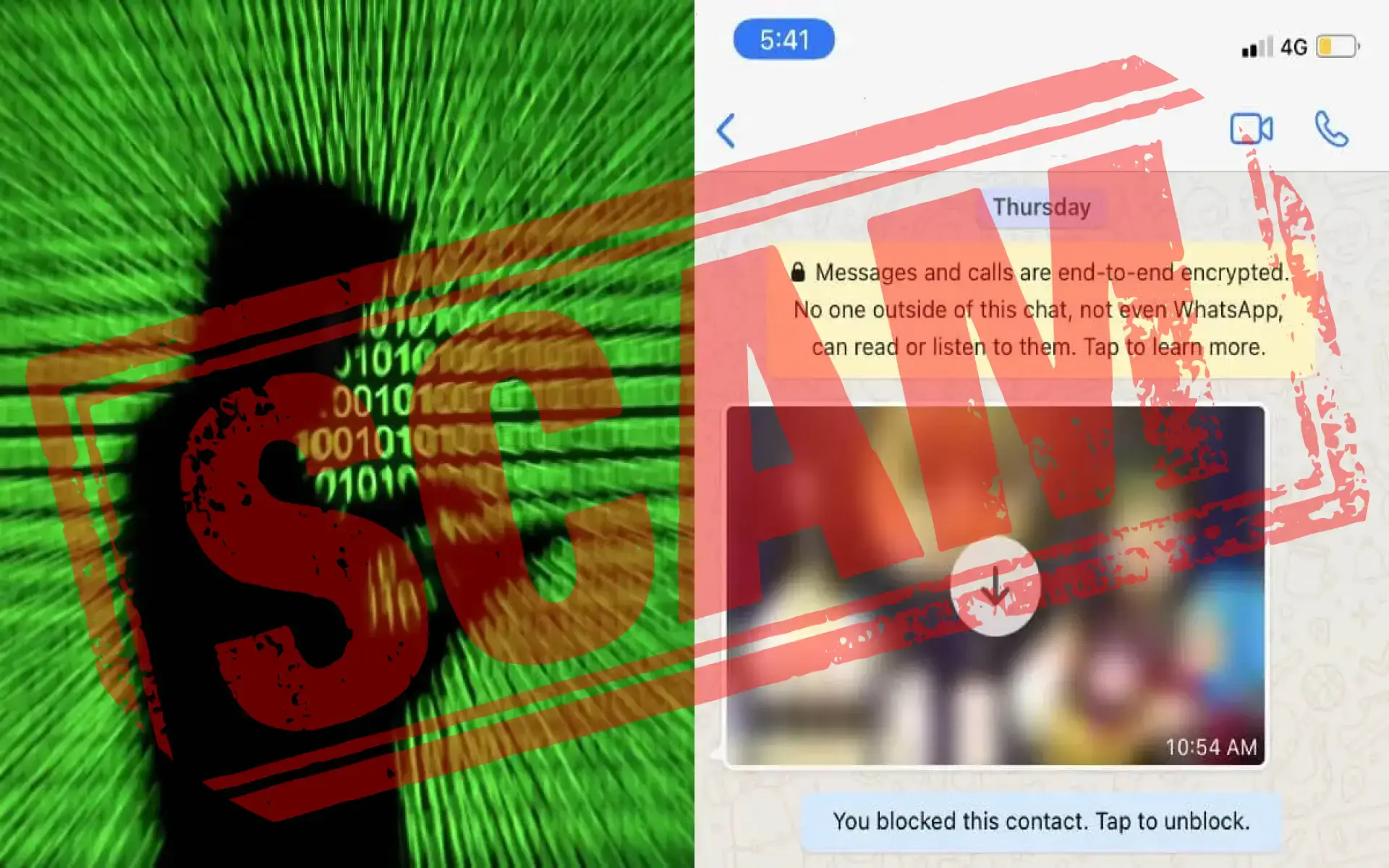
The scammers share photos or videos using social media platforms like WhatsApp, Telegram, Facebook Messenger, Instagram in the name of an invite or an offer, the Department of Telecommunications (DoT) said in a statement.
Users see new offers or invites and download those photos or videos on the phone. By doing this, scammers inject dangerous viruses into users’ phones and take access to their phones.
Hacking phones through Photos, Videos
Many times users are not even aware and photos and videos are automatically downloaded to their phones through apps like WhatsApp, Instagram.
Such users will have to go to the settings of these apps and turn off the option of automatic download of photos and videos.
This will be beneficial for the users. Firstly, the data of their phones will not be lost quickly and secondly, such scams will be avoided.
How to get rid of Steganography?
The Department of Telecommunications has prohibited users from downloading photos, audio and video from any unknown number.
Along with such media files, scammers also share a link to the user. Knowingly or unknowingly, users open these links, through which access to the user’s phone reaches the hackers.